PKI, or public key infrastructure, encompasses everything used to establish and manage public key encryption. This includes software, hardware, policies, and procedures that are used to create, distribute, manage, store, and revoke digital certificates.
A digital certificate cryptographically links a public key with the device or user who owns it. This helps to authenticate users and devices and ensure secure digital communications.
PKI is one of the most common forms of internet encryption, and it is used to secure and authenticate traffic between web browsers and web servers. It can also be used to secure access to connected devices and internal communications within an organization.
Public key infrastructure has a long history of securing and authenticating digital communications with two main goals: to ensure the privacy of the message being sent and to verify that the sender is who they claim to be.
Public key infrastructure (PKI) is a system of technologies, policies, procedures and people that enables secure digital communications and provides cryptographic security for electronic transactions. PKI establishes and governs the process of generating, distributing, managing and revoking digital certificates that link a public key to an entity such as a person, organization or device.
PKI enables trusted and private communications over insecure public networks like the internet by establishing the identity of entities involved It’s one of the most common forms of internet encryption and authentication.
In this article, we’ll explain what PKI is, why it’s important, how it works, its components, types of PKI, and more.
What is PKI?
PKI provides the basis for trusting digital communications and electronic transactions It enables two parties to securely communicate over an insecure channel by verifying identities and facilitates data encryption to ensure confidentiality and integrity
PKI establishes a link between a public key and its owner to prevent impersonation It does this through digital certificates issued and verified by a trusted third-party Certificate Authority (CA)
The core elements of a PKI include:
- Digital certificates – contain identity credentials and public key to authenticate and verify identity
- Public and private key pairs – used for encryption and decryption
- Certificate Authorities – issue and revoke digital certificates
- Registration Authorities – verify identity and credentials for certificate issuance
- Repositories and directories – allow access to certificates and certificate revocation lists
- Certificate policies and practice statements – govern PKI processes and procedures
PKI provides trust services related to confidentiality, integrity, authentication and non-repudiation. It enables secure electronic transfer of information for activities like e-commerce, online banking and confidential communication.
Why is PKI Important?
PKI is essential for securing communications and transactions where basic password authentication is insufficient. PKI establishes trust in digital identities which provides:
- Privacy – Messages remain confidential through encryption using public-private key pairs
- Authentication – Digital signatures and certificates verify identity of sender
- Integrity – Detects any changes to message contents through hashing algorithms
- Non-repudiation – Senders cannot deny sending the message as their private key is used
Without PKI, there would be no trusted way to conduct secure online transactions, communications and interactions. PKI enables business critical activities like online banking, e-commerce, confidential email and protects access to connected devices and networks.
How Does PKI Work?
PKI uses public-key cryptography to enable trust and security. Here’s an overview of how PKI works:
- A user generates a public-private key pair and requests a digital certificate from a CA
- The CA verifies the user’s identity through the Registration Authority (RA)
- The CA issues a certificate binding the user’s identity to their public key
- The user retains the private key secretly while the public key is embedded in the certificate
- When the user wants to communicate with another party, they exchange certificates
- The public keys in the certificates are used to encrypt and decrypt messages
- The authenticity and integrity of messages are validated through the certificates
This establishes an encrypted channel allowing the parties to communicate securely. The private keys are only known to their owners so messages can only be decrypted by intended recipients.
Digital Certificates
Digital certificates allow the public key to be trusted. They contain information about the key owner’s identity and public key signed by the issuing CA.
Certificates adhere to X.509 standard and include fields like:
- Issuer – CA that issued the certificate
- Subject – Identity of key owner (individual, organization, device)
- Public key – Key used to encrypt messages
- Validity period – Certificate expiration date
- Signature – CA digital signature to authenticate origin
Public and Private Keys
Public key cryptography uses key pairs for encryption and decryption.
- Public key – Shared openly, used to encrypt messages
- Private key – Kept secret, used to decrypt messages
Public keys allow anyone to encrypt messages to the key owner. But only the paired private key can decrypt them. This enables confidentiality.
Private keys also create digital signatures which authenticate the sender’s identity. The signature is verified using the public key.
Certificate Authorities
CAs are trusted third parties that issue, manage and revoke digital certificates. They validate identities and issue certificates binding entities with their public key.
CAs digitally sign certificates using their own private key. Trust in the user’s certificate relies on trusting the CA’s signature.
CAs can be independent or part of private organization PKIs. Browsers and OSs come with pre-installed trusted root CA certificates.
PKI Components
The core components of a PKI include:
Certificate Authority – Issues, publishes, manages and revokes digital certificates. Acts as the trusted entity at the center of the PKI.
Registration Authority – Verifies and authenticates identity of entities requesting certificates from the CA. Can be separate from CA or part of it.
Certificate Database – Repository containing all issued certificates and revocation lists. Allows certificates to be retrieved and verified.
Certificate Policy – Defines the PKI’s practices, procedures and requirements. Allows external parties to gauge the PKI’s trustworthiness.
Types of PKI
There are several approaches and architectures for implementing PKI:
Hierarchical PKI
Most common type with a centralized CA issuing certificates under its trusted root certificate. Allows a chain of trust with every certificate verifiable via the root CA’s certificate. Used in commercial CAs and enterprise PKIs.
Mesh PKI
Decentralized model where CAs cross-certify each other as equals to create a mesh topology. Provides redundancy since compromise of one CA doesn’t impact trust in other CAs. Used in government, banking and defense.
Bridge PKI
Hybrid model combining hierarchical and mesh PKI. Root CAs cross-certify while lower-level CAs have hierarchical relationship. Provides advantages of both models. Used across organizations and industry groups.
Web-of-Trust
Decentralized model where individuals sign each other’s keys to establish authenticity in a web-of-trust. Doesn’t rely on CAs. Used in cases like PGP encryption. More vulnerable to compromise than hierarchical PKIs.
Real-World Applications
PKI is extensively used to secure internet communications and online transactions, including:
-
HTTPS – PKI enables TLS/SSL encryption which secures HTTPS sites. CAs issue SSL/TLS certificates to websites.
-
Code Signing – Signing software, binaries and scripts to verify authenticity and integrity. Prevents distribution of malware.
-
Email Security – S/MIME protocol uses PKI for email encryption, authentication and signing.
-
Document Signing – Applying digital signatures to documents like contracts and invoices to ensure authenticity, non-repudiation and integrity.
-
Device Authentication – Machine identities use PKI to authenticate and authorize connected devices like IoT and medical equipment.
-
VPN Access – Issuing certificates to allow employees secure remote access to enterprise networks and resources.
Benefits of PKI
PKI provides a robust framework for trust in digital environments by delivering:
-
Security – Encryption, signatures and certificates prevent interception, impersonation and tampering
-
Trust – Identities and transactions can be trusted by relying on credentials issued from trusted CAs
-
Convenience – No physical documents or face-to-face processes required for transacting online
-
Compliance – PKI facilitates meeting regulations around data protection and transaction records
-
Scalability – Certificate automation allows easy rollout across users and systems
Limitations of PKI
While PKI is critical for security, it has some limitations:
- Certificate management can be complex with large user populations
- Compromise of root CA undermines all certificates issued by it
- Certificate revocation is challenging to execute instantly across systems
- Requires technical expertise and resources to operate PKIs
- External CAs represent single point of failure outside organization’s control
PKI provides the foundation for trusting identities and securing communications in the digital world. As use of online services and connected devices grows exponentially, PKI will continue playing a pivotal role in protecting privacy and transactions.
With growing cyber threats and regulations, building robust PKIs with efficient certificate lifecycle management will be crucial for enterprises and government agencies. Understanding PKI concepts allows organizations to deploy solutions that balance security, cost and user experience.
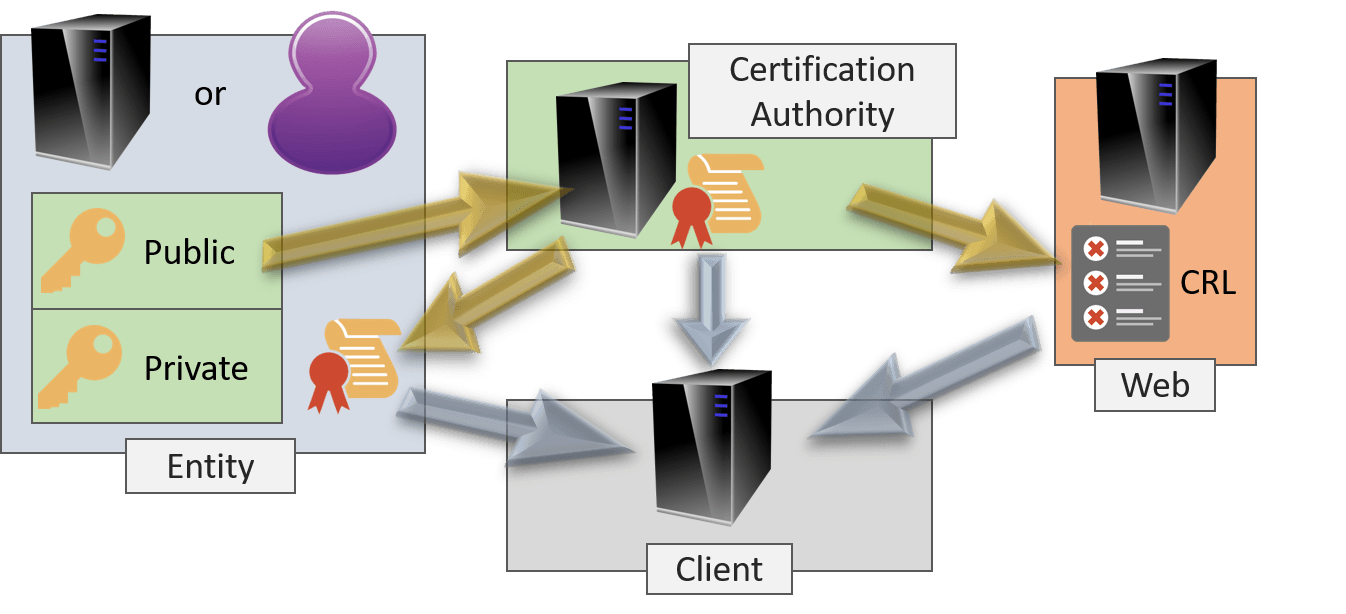
Understanding how PKI works
Public key infrastructure uses asymmetric encryption methods to ensure that messages remain private and also to authenticate the device or user sending the transmission.
Asymmetric encryption involves the use of a public and private key. A cryptographic key is a long string of bits used to encrypt data.
The public key is available to anyone who requests it and is issued by a trusted certificate authority. This public key verifies and authenticates the sender of the encrypted message.
The second component of a cryptographic key pair used in public key infrastructure is the private, or secret, key. This key is kept private by the recipient of the encrypted message and used to decrypt the transmission.
Complex algorithms are used to encrypt and decrypt public/private key pairs. The public key authenticates the sender of the digital message, while the private key ensures that only the recipient can open and read it.
The core of a public key infrastructure is trust. It is important for a recipient entity to know without a doubt that the sender of the digital certificate is exactly who they claim to be.
Trusted third-party CAs can vouch for the sender and help to prove that they are indeed who they say they are. Digital certificates are used to verify digital identities.
Digital certificates are also called PKI certificates or X.509 certificates. A PKI certificate offers proof of identity to a requesting entity, which is verified by a third party and works like a digital passport or driver’s license.
The PKI certificate will contain the following:
- Distinguished name (DN) of the owner
- Owner’s public key
- Date of issuance
- Expiration date
- DN of the issuing CA
- Issuing CA’s digital signature
What is public key infrastructure (PKI)?
Public key infrastructure is an important aspect of internet security. It is the set of technology and processes that make up a framework of encryption to protect and authenticate digital communications.
PKI uses cryptographic public keys that are connected to a digital certificate, which authenticates the device or user sending the digital communication. Digital certificates are issued by a trusted source, a certificate authority (CA), and act as a type of digital passport to ensure that the sender is who they say they are.
Public key infrastructure protects and authenticates communications between servers and users, such as between your website (hosted on your web server) and your clients (the user trying to connect through their browser. It can also be used for secure communications within an organization to ensure that the messages are only visible to the sender and recipient, and they have not been tampered with in transit.
The main components of public key infrastructure include the following:
- Certificate authority (CA): The CA is a trusted entity that issues, stores, and signs the digital certificate. The CA signs the digital certificate with their own private key and then publishes the public key that can be accessed upon request.
- Registration authority (RA): The RA verifies the identity of the user or device requesting the digital certificate. This can be a third party, or the CA can also act as the RA.
- Certificate database: This database stores the digital certificate and its metadata, which includes how long the certificate is valid.
- Central directory: This is the secure location where the cryptographic keys are indexed and stored.
- Certificate management system: This is the system for managing the delivery of certificates as well as access to them.
- Certificate policy: This policy outlines the procedures of the PKI. It can be used by outsiders to determine the PKI’s trustworthiness.
Tech Talk: What is Public Key Infrastructure (PKI)?
What is PKI (public key infrastructure)?
PKI (public key infrastructure) is the underlying framework that enables entities — users and servers — to securely exchange information using digital certificates.
What is public key infrastructure?
Public key infrastructure uses asymmetric encryption methods to ensure that messages remain private and also to authenticate the device or user sending the transmission. Asymmetric encryption involves the use of a public and private key. A cryptographic key is a long string of bits used to encrypt data.
What is a public key?
The public key is available to anyone who requests it and is issued by a trusted certificate authority. This public key verifies and authenticates the sender of the encrypted message. The second component of a cryptographic key pair used in public key infrastructure is the private, or secret, key.
What technology enables PKI?
The core technology that enables PKI is public key cryptography, also known as asymmetric encryption. Asymmetric encryption is used to create a public key, pair it with a private key, and create an association between the two. Plain text is encrypted and converted to ciphertext by an encryption key.