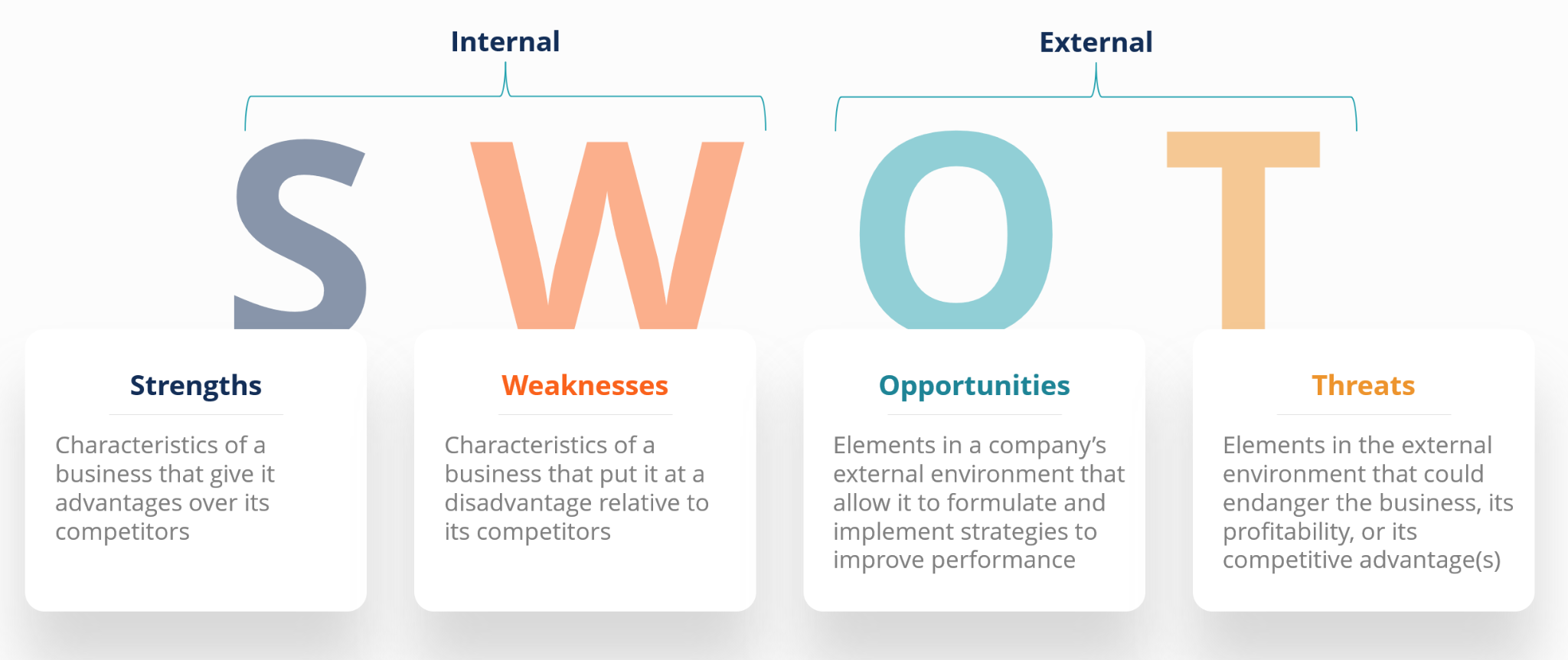
SWOT analysis is a strategic planning technique used to evaluate the Strengths, Weaknesses, Opportunities, and Threats involved with a project or business While opportunities help boost growth, threats can potentially derail your efforts. Properly assessing threats in a SWOT analysis is crucial for risk mitigation.
In this comprehensive guide, we’ll cover what constitutes a SWOT threat, real-world examples, and strategies to combat the threats facing your business.
What is a Threat in SWOT Analysis?
A threat refers to any external or internal factor that can negatively impact your business’s operations competitiveness or ability to execute strategies. These hazards or risks have the potential to damage productivity, decrease sales, incur financial losses, and essentially hinder your chances of achieving core objectives.
Threats are one of the factors weighed in a SWOT analysis, along with strengths, weaknesses and opportunities. Some examples of threats include:
- Competitors introducing superior products
- Rising production costs
- Natural disasters disrupting supply chains
- Shifts in consumer preferences
- Cybersecurity issues
- New regulations
Threats combined with weaknesses often signal greater risks, since vulnerabilities expose you more to their effects. But even standalone threats need to be planned for due to their potential damage.
Types of Threats in SWOT Analysis
Threats in a SWOT analysis generally emerge from factors in the external environment or your internal operations Here are some common categories of threats
Competitive Threats
- Competitors launching better products
- Competitors lowering prices
- Aggressive marketing from a rival brand
- Competitors forging partnerships and alliances
Economic Threats
- Rising costs of supplies, inventory, or shipping
- Shortages of skilled talent
- Declines in consumer spending during recessions
Market Threats
- Changing consumer behaviors, tastes, and preferences
- Emergence of substitute products
- Decreasing product differentiation
Technological Threats
- Disruptive innovations rendering your products obsolete
- Cyber threats like hacking, malware or data breaches
- Disruptions to infrastructure or IT systems
Regulatory Threats
- New laws, policies or regulations
- Increased compliance burden
- Shifts in political conditions
Operational Threats
- Inadequate disaster preparedness
- Supply chain disruptions
- Quality control issues
- Labor strikes or turnover
This diverse mix of hazards makes threat identification complex. The next section provides real examples across these categories.
Examples of Threats in SWOT Analysis
Here are some practical examples of threats broken down by source:
Competitive Threat Examples
- Coca Cola faces aggressive marketing from rival Pepsi
- Uber’s market share declines as Lyft expands to new cities
- Luxury hotel chain loses customers to a new boutique hotel nearby
Economic Threat Examples
- An airline’s fuel and operational costs rise rapidly
- A software firm struggles to recruit programmers due to tech talent shortage
- A retailer sees lower sales due to consumers cutting spending in a recession
Market Threat Examples
- Kodak clings to film photography as digital cameras gain popularity
- DVD rental stores close as media streaming expands
- Print newspapers and magazines lose subscribers to online news
Technological Threat Examples
- Netflix pivots to streaming as customers abandon DVD rentals
- Hotels adopt cybersecurity measures as data breaches threaten customer loyalty
- Carmakers enhance connectivity and self-driving features as preferences shift
Regulatory Threat Examples
- Social networks like Facebook and Twitter face regulations on data use and content moderation
- Ride-sharing apps must comply with complex emerging transportation laws
- Food and beverage brands adjust packaging and marketing amid new labeling rules
Operational Threat Examples
- A severe storm disrupts supply chains and inventory for a retailer
- Staffing issues lead to poor service at a restaurant, causing a sales decline
- A tech company experiences an outage that impacts applications and uptime
As these examples demonstrate, threats run the gamut from competition and market evolution to operational risks and compliance factors. The SWOT analysis process prompts you to delve into all these hazards.
How to Manage Threats in SWOT Analysis
Simply identifying threats is not enough. Once you uncover them through SWOT analysis, you need to actively manage and mitigate them. Some strategies include:
-
Have contingency plans – Develop backup strategies you can deploy if certain threats materialize.
-
Focus on agility – Design nimble operations that allow you to quickly adapt to changing market conditions.
-
Build in redundancies – Mitigate single points of failure in supply chains or IT systems through multi-sourcing, backups and spare capacity.
-
Monitor early warning signs – Track metrics tied to potential threats to prepare ahead of time.
-
Improve cyber defenses – Implement robust cybersecurity measures and protocols.
-
Cross-train employees – Reduce operational risks from turnover by training employees across different functions.
-
Keep compliance rigorous – Maintain rigorous adherence to regulations through checks and balances.
-
Insure adequately – Transfer risks through comprehensive insurance policies covering likely threats.
-
Conserve financial reserves – Maintain rainy day funds and reserves to endure periods of economic decline or other crises.
Proactive threat management reduces the likelihood and impact of potential catastrophes derailing your plans. View them as unavoidable obstacles to prepare for rather than simply accept.
Tips for Assessing Threats in SWOT Analysis More Effectively
Here are some tips to enhance how you identify and analyze threats during the SWOT process:
-
Involve a diverse team – Get input from employees in different functions and at various levels of authority. They may notice threats unknown to top executives.
-
Solicit external perspectives – Talk to customers, vendors, contractors and industry experts to identify threats you may have overlooked.
-
Research competitors – Study the strategies, products and partnerships of competitors to pinpoint emerging competitive threats.
-
Stay up to date on market changes – Monitor industry news and segment trends to detect shifts that may threaten your current products or processes.
-
Conduct risk assessments – Dedicate time for structured risk analysis outside of SWOT brainstorming to surface a comprehensive list of threats.
-
Re-evaluate frequently – Refresh your SWOT analysis at least annually to account for new threats that have arisen.
Making threat identification a collaborative, continuous process enhances your readiness to confront the ever-evolving challenges businesses face.
SWOT Analysis Threats vs. Weaknesses
Threats in SWOT analysis get conflated with weaknesses at times. But while related, these two factors are distinct:
Weaknesses – Internal flaws in your operations, strategy, or competitiveness driven by insufficiencies in skills, resources, systems, or functions.
Threats – External or internal risks that could negatively impact your operations, competitiveness, or strategy execution.
Weaknesses are vulnerabilities you must shore up through improvement initiatives. Threats are hazards you must monitor and prepare contingency plans for. Being clear on this difference helps distinguish appropriate responses.
For example, an aging product line near the end of its lifecycle would be classified as a weakness, whereas emerging lower-priced competitive products would constitute a threat. Recognize when conditions represent risks to guard against rather than shortcomings to simply fix.
Threat identification and mitigation are pivotal for strategic planning and risk management. Rather than view threats in SWOT analysis as minor footnotes, recognize their potential to upend your goals for growth and progress. Committing adequate time and resources to uncovering and responding to them is an investment well rewarded through improved resilience.
With a robust action plan for managing SWOT threats, you have a greater chance of capitalizing on opportunities and strengths, while preventing risks from jeopardizing your way forward. Through vigilant awareness and proactive precautions, your organization can confidently navigate uncertainties.
Using SWOT analysis in your business
You should consider doing a SWOT analysis to give you a framework for understanding the state of your business and where you have opportunities for growth or fixing any faults in your operation.
To conduct a SWOT analysis, you must look at both the internally and externally focused activities of your business.
Internally focused activities are matters generally under the businesss control, including:
- internal operations
- marketing and sales
- financial management
- staffing and human resources
- customer service
- quality assurance.
You can use the SWOT analysis tool (see below) to identify current strengths and weaknesses in your internally focused activities.
To assist your analysis, consider:
- conducting quarterly internal reviews
- brainstorming with your team
- checking business processes
- tracking business performance and metrics.
Externally focused activities are the activities that affect your business but are generally outside its control, including:
- supplier operations
- tenders and grants
- competitors
- politics
- the social and natural environment
- global trade
- financial markets.
You can use the SWOT analysis tool (see below) to identify opportunities and threats for externally focused activities.
To assist your analysis, you might also consider:
- researching trends, reports and industry data
- reading newspapers and journals
- working with mentors and advisers
- attending business events and conferences
- meeting with suppliers and government
- attending research tours of other states and countries.
Reasons for using a SWOT
You can use a SWOT analysis to help you review your entire business, but you can conduct an analysis focussing on 1 or 2 specific issues.
SWOT analysis can:
- help you create or update your business plan
- help you decide whether to introduce a new product or service to the market
- be part of your regular strategic planning review (quarterly, half-yearly or yearly).
A SWOT analysis should generate a brief list of issues relevant to the 4 categories—strengths, weaknesses, opportunities and threats.
The analysis of these issues helps the business make meaningful changes. For example, if the SWOT analysis has indicated a staffing weakness, a more detailed human resourcing plan may be required.
3 Questions to Ask yourself to Determine the Threats in a SWOT Analysis
Why is it important to recognize threats in a SWOT analysis?
Recognizing threats is important because it can help you overcome potential business challenges. In this article, we discuss what SWOT analysis threats are, look at nine common threats in business and provide some tips to help you manage them. What are threats in a SWOT analysis?
What are threats in SWOT?
Threats in SWOT are areas with the potential to cause problems. Different from weaknesses, threats are external and out of your control. This can include anything from a global pandemic to a change in the competitive landscape. Here are a few questions to ask yourself to identify external threats:
What types of threats can be used for risk identification & SWOT analysis?
The following are examples of threats that can be used for risk identification and swot analysis. The potential actions of a competitor are the most common type of threat in a business context. For example, a competitor who copies your new product thus decreasing its unique value on the market. Loss of talent or an inability to recruit talent.