Looking for the best Red Hat Linux interview questions and answers? Red Hat Linux is the most popular Linux platform in the world, and big companies like Twitter, Sony, Google, IBM, Juniper Networks, and more use it. It is important to prepare for the Red Hat Linux interview if you want to get a job as a Linux administrator or engineer at one of these companies.
This guide is your go-to when preparing for technical interview rounds. This book has more than 30 Red Hat Linux interview questions and answers that can help you get ready to become a highly sought-after Red Hat Linux expert.
So, without further ado, here are some Red Hat Linux interview questions and answers that you might be asked in technical interviews.
Red Hat is one of the leading providers of open source software solutions best known for its Red Hat Enterprise Linux operating system. With its wide range of products and services focused on Linux virtualization, cloud computing, storage, and more, Red Hat has become a preferred choice for many enterprise organizations.
If you have an interview coming up for a job role related to Red Hat technologies you need to be prepared to answer some common Red Hat interview questions. Going through a list of frequently asked questions and sample answers will help you get an idea of what to expect in a Red Hat interview. In this article we provide answers to some of the top and commonly asked Red Hat interview questions.
1. How to Verify the Uptime of a Linux Server?
To verify the uptime of a Linux server, you can use the uptime command. This will display the current time, how long the system has been running, and the system load averages.
For example:
$ uptime10:45:34 up 23 days, 34 min, 1 user, load average: 0.00, 0.01, 0.05This shows the system has been up for 23 days 34 minutes.
Some other ways to check uptime include:
cat /proc/uptime– Show uptime in secondswho -b– Show last system boot timelast reboot– Show reboot history
So in a Red Hat interview, you should be able to explain the uptime command and different ways to verify server uptime.
2. Explain About the Red Hat Network?
The Red Hat Network (RHN) is a web-based system management platform provided by Red Hat. It enables system administrators to manage Red Hat Enterprise Linux installations and provides various services such as:
- Software package updates and errata
- Subscription management
- Hardware inventory tracking
- Proactive monitoring and alerting
- Configuration management
RHN has a web-based user interface and command line tools that allow administrators to manage systems and keep them updated with the latest packages, security fixes, and enhancements.
Key components of RHN include the RHN Server, Satellite Server, Proxy Server, and Client tools. It offers robust functionality for managing both physical and virtual Red Hat Enterprise Linux environments.
3. Explain the Objectives of RedHat Linux?
Some of the key objectives and goals of the RedHat Linux operating system are:
- Provide a high-performance Linux distribution suitable for enterprise use
- Make Linux easy to use for novice and advanced users alike
- Offer support, services, and training on Linux for businesses
- Maintain strict compatibility with Linux standards
- Collaborate with hardware vendors to certify Linux on a wide range of architectures
- Develop innovative new technologies under open source model
- Simplify maintenance and upgrades with yum package manager
- Enhance security with SELinux and other features
- Support multiple architectures like x86, x86-64, Power, ARM, IBM Z
- Adhere to open source philosophy and community-driven development
4. Explain the Functionality of a Puppet Server?
Puppet is a popular open source configuration management and automation tool by Puppet Labs.
A Puppet server is the central component that manages the configuration of managed nodes called Puppet agents.
Key functions of a Puppet server include:
-
Store Puppet code and data: The Puppet server stores all the Puppet manifests, modules, and other data required to manage the infrastructure.
-
Compile Puppet code: It compiles the Puppet code written in the Puppet DSL into a catalog that applies to each agent node.
-
Distribute configuration catalogs: The compiled catalogs are distributed by the Puppet server to the connected Puppet agents.
-
Provide reports: Agents send back reports to the Puppet server after applying the catalogs so admins can track compliance.
-
Enforce desired state: If any resource drifts away from the desired state, Puppet will automatically correct it.
-
Scaling infrastructure: Puppet servers can be scaled using compile masters and PuppetDB for large deployments.
5. Explain the Difference Between Umask and Ulimit?
Umask and ulimit are two concepts related to managing resource limits in Linux:
-
umask sets the default file permission bits for newly created files. It uses a 3 digit octal value to specify permissions – for example, 022 sets default permissions to 755 for files and 775 for directories.
-
ulimit sets user limits on things like number of open files, processes, memory usage etc. Common options are -n for open files, -u for processes, -l for max memory usage.
Key differences:
-
umask applies to file permissions, ulimit is for system resource limits per user/process.
-
umask uses an octal value, ulimit takes options like -n, -u etc and numeric values.
-
umask sets the default, ulimit sets a hard limit.
-
umask applies to all users, ulimit can be set per user/process.
-
umask is set with the umask command, ulimit uses the ulimit command.
6. Explain the Run Levels and How to Alter Them?
Red Hat Enterprise Linux has 7 runlevels from 0 to 6 plus the GUI mode. Each runlevel configures a different system state:
- 0: Shut down the system
- 1: Single user mode with limited networking
- 2: Multiuser with no NFS and network services
- 3: Full multiuser mode with console logins and networking
- 4: Not used/user-definable
- 5: Full multiuser with GUI login screen
- 6: Reboot the system
The default runlevel is 3 for console-based startup and 5 for graphical startup.
You can check the default and previous runlevel using the runlevel command.
To change the default runlevel permanently, edit the /etc/inittab file and set the default runlevel.
To temporarily boot into a different runlevel, edit the kernel boot parameters in the bootloader configuration and specify the runlevel.
For example, to boot into single user mode runlevel 1, append 1 to the kernel parameters in /etc/grub.conf.
7. How to Create Users and Manage Permissions in Linux?
To create users in Red Hat Enterprise Linux, the useradd command is used. For example:
# useradd johnThis will create a user named john with default settings.
To set a password for the user:
# passwd johnUser permissions are managed using Linux file permissions and ACLs.
File permissions can be changed using chmod. For example:
# chmod 600 file.txtSets read-write for owner, no access for others.
ACLs allow setting permissions for specific users and groups. For example:
# setfacl -m user:john:rw file.txtGives read-write access to john for file.txt.
User group permissions can be managed by adding users to groups like wheel for admins. User and group info is stored in /etc/passwd and /etc/group.
8. How To Install a Package from a YUM Repository?
YUM (Yellowdog Updater Modified) is the package manager used by Red Hat Linux systems.
To install a new package from a YUM repository:
- Search for the package:
# yum search <keyword>- Install the package:
# yum install packagenameYUM will resolve all dependencies and install the package along with requirements.
- Verify the package installed:
# rpm -qi packagenameYUM repositories can be added by creating .repo files in /etc/yum.repos.d/ with details like URL, name, and enabled status. RHEL systems include pre-configured repos like EPEL.
So YUM and its repositories provide an easy way to find and install packages on Red Hat based systems.
9. How To Configure Apache Web Server on Linux?
Apache httpd is a popular web server platform available on Linux. Here are the key steps to configure Apache on Red Hat Linux:
- Install Apache if not already installed:
Red Hat Linux Interview Questions and Answers for Freshers
1. What is meant by Red Hat Linux?
Linux is one of the most commonly used operating systems across the globe. It is even a more popular choice than a Windows operating system. Thanks to it being an open-source platform. On top of that, it is also a free and economical operating system.
Other important points include that it is user-friendly.
One company that distributes the Linux operating system is Red Hat. In fact, it is one of the most reliable ones. It can do the following:
- It can help scale up existing applications.
- It helps new technologies come out, like containers, the cloud, automation, virtual environments, SDKs, microservices, and so on.
2. What are some of the benefits of Red Hat Linux?
The following are some of the significant benefits of the Red Hat Linux:
- Red Hat Linux is an open-source software.
- It offer a GUI (Graphic User Interface) Operating system.
- Open-source technical support is also available, which is different from other Linux distributions that charge a lot to fix technical problems.
- It helps in completing basic command-line tasks.
3. What is meant by Red Hat network?
To conclude, Red Hat network is a system management platform. It particularly helios the users with an effective lifecycle management of various apps and operating systems. The other features of the Red Hat network include:
- Installing and setting up fresh Linux systems.
- Handling of configuration files.
- System reconfiguration for hosted and satellite deployment architectures.
- System updates.
- Performance evaluation.
4. How can you verify the uptime of a Linux server?
In order to verify the uptime of a Linux server, you can use command line. The best command is the ‘uptime’ command. By running this command, you get to know the time span of how long the Linux box ran. Other commands you can use include:
5. How can you rename a file in Red Hat Linux?
You can follow the below mentioned steps to rename a file in Red Hat Linux:
- First of all, open the Linux shell command line.
- Use the “mv” command in the command line interface.
- This program will show you both the original files and the ones with new names.
- Before changing the names of the files, you should make sure that all of the settings are correct.
- Sometimes, a user forgets to check few parameters. In such cases,, the command prompts you to recheck them.
6. What is a puppet server?
A server that use an operating system similar to Unix is known as a puppet server.
This business application is great for managing setups overall.
The significant functionalities of the puppet server includes the following:
- There is no cost to use this application, and it is fully automated to be more accurate.
- In this way, you can use codes to tell puppet agents what to do.
- You can use puppet code to do many things, like changing user accounts, making sure files have the right permissions, and installing new software.
7. What is meant by LILO?
A Linux boot loader is called LILO. It is primarily used to start the Linux operating system’s activities by loading it into main memory.
8. What is meant by SELinux?
SELinux is an acronym for Security-Enhanced Linux. As the name suggests, it keeps the server safe from bad things like misconfigurations or daemons that have been hacked. Security policy tells server applications how to access certain files or files that they are allowed to access. It also sets limits on what applications can do.
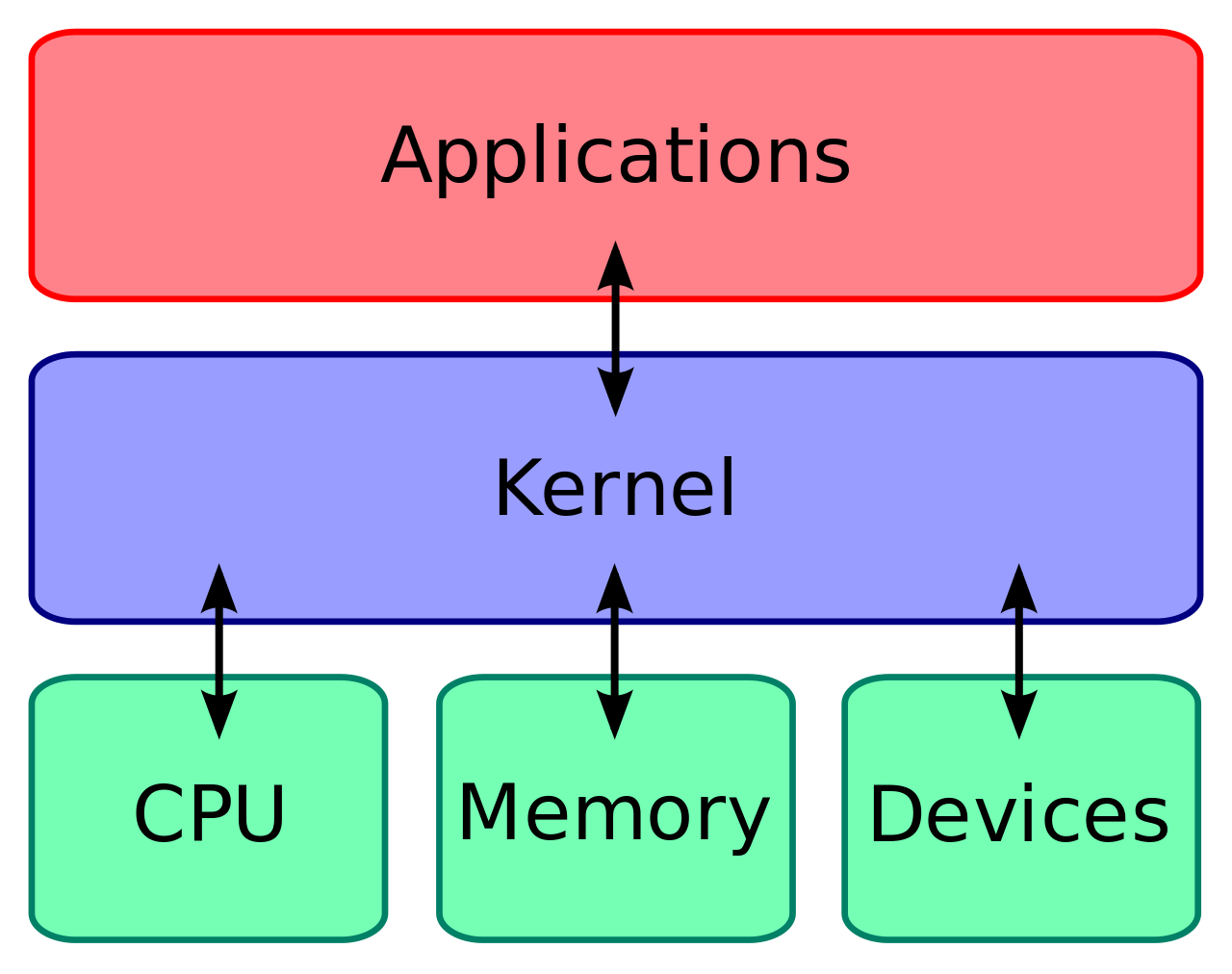
9. What do you understand by Linux Kernel?
The heart of Linux operating systems is the Linux Kernel. The Linux Kernel is a low-level piece of systems software whose main job is to take care of hardware resources for the user. Additionally, it serves as a user interface for interactions at the user level.
10. How can you change the User Password?
Users can modify their passwords by using the command “passwd”. The command must be executed through the prompt while the current password is being input. Type the new password next and you are good to go!.
11. Mention the basic components of Linux.
The following are the main components of Linux:
- Linux kernel
- Shells
- Graphical User Interface (GUI)
- System utilities
- Application program
12. What do you understand by CLI?
Command Line Interface, or CLI, is an abbreviation. People can use this interface to tell the computer what to do by typing in logical commands. CLI provides more versatility. However, some users who are already used to GUI find it hard to remember the instructions and the attributes that go with them.
13. What are the different types of Linux user modes available?
There are two main types of user modes available:
- Graphical User Interface (GUI)
- Command Line Interface (CLI)
14. How can you open a command prompt to pass a command?
You can follow the following quick steps to open the command prompt:
- The command prompt is present in the default shell.
- You need to press Ctrl-Alt-F1. If you have a Mac, you can also run the bash scripts with the Terminal app.
- After that, you can get to the command line interface (CLI) and run all the commands you need.
15. Which is more secure: Windows or Linux? And Why?
Linux Operating systems are more secure as compared to the Windows operating system. The reasons are mentioned below:
- The Linux operating system has many work environments, all of which are virus-protected. These include Linux Mint, Debian, Arch, and others.
- It keeps a log history so that you can quickly look at the details of the system files later.
- Linux has a feature called Iptables that checks the security of the system.
- A smaller number of people using Linux will make it safer than other operating systems.
- The Linux system can only be used by a few people. The virus can only possibly harm a few files instead of the whole system because of this.
- To keep their systems safe from attacks, Linux users must finish the steps before they can access the files.
16. What are the various available run levels in Linux?
The various run levels that are present in Linux are mentioned below:
- System of halt (attempted system shutdown)
- There won’t be an NFS option, but there will be one for multiple users.
- Setting for individual users
- The whole multi-user mode (based on the text)
- Graphical user interface mode for numerous users
- Unused
- Launch the computer again
17. How can you install rpm packages?
We can install the rpm packages by using the command line. The yum and rpm command lines made it easy to install on the Red Hat Linux operating system.
18. What is meant by load balancing cluster?
The concept of load balancing cluster could be understood from the following pointers:
- For load balancing, the cluster is used to spread the work among the cluster nodes.
- It works when the cluster sends the service request to a different cluster node.
- Because more nodes can be added based on load, this cluster offers scalable capabilities at a reasonable price.
- If a node in this cluster has a problem, it will figure out what the problem is and then send the requests to the other nodes that are available. This way, people outside the cluster won’t be able to see the node fall apart.
19. What us a storage cluster?
When a task is performed by a collection of two or more computers, those are known as clusters. The various clusters are mentioned as follows:
- High availability
- High performance
- Load balancing
The main features of the storage cluster are:
- A storage cluster gives you a perfect and consistent view of the file systems on all the servers in the group.
- It lets servers read from and write to a shared file system at the same time.
- It also makes storage management better by speeding up and limiting the process of installing and packaging applications.
20. How can you know which version of Red Hat are you using?
Using the ‘cat /etc/Redhat-release‘ command, you may find out the Red Hat version.
$999 $499 only For All Access Pass Today! USE PROMO CODE : LIMITED







Looking for the best Red Hat Linux interview questions and answers? Red Hat Linux is the most popular Linux platform in the world, and big companies like Twitter, Sony, Google, IBM, Juniper Networks, and more use it. It is important to prepare for the Red Hat Linux interview if you want to get a job as a Linux administrator or engineer at one of these companies.
This guide is your go-to when preparing for technical interview rounds. This book has more than 30 Red Hat Linux interview questions and answers that can help you get ready to become a highly sought-after Red Hat Linux expert.
To make things easier for you, this guide is divided into two sections. These include:
- Red Hat Linux interview questions for freshers
- Red Hat Linux interview questions for experienced professionals
So, without further ado, here are some Red Hat Linux interview questions and answers that you might be asked in technical interviews.
Red Hat Interview Preparation
FAQ
How many rounds of interview are there in Red Hat?
What are the easiest Red Hat Linux system administrator interview questions?
Give us a short description. Answer: One of the easiest Red Hat Linux System Administrator interview questions in the interview. The answer is very simple. Just tell the recruiter that bootloader boots the operating system. Besides, it takes the decision about the kernel from which the operating system will boot.
What is the interview process like at Red Hat?
I interviewed at Red Hat (Raleigh, NC) There was a phone interview followed by a panel interview. Process was smooth and easy. Recruiters were very informative and helpful. Questions based on previous work experience and educational background. Describe your role at your previous worksite. I applied through an employee referral.
What is the Red Hat hiring process?
The Red Hat hiring process typically begins with a phone screening or initial interview with a recruiter, followed by one or more technical interviews with senior team members or managers. Candidates may also undergo a panel interview with the consulting team leaders or participate in a group interview.
Will there be a technical interview at Red Hat in 2024?
I interviewed at Red Hat in Apr 2024 I got a call from one of the redhat recruiter and he said there will be 2 technical interview and 1 hr . But after completing 2 technical rounds he said one more technical interview will be there. I have cleared that as well.
